In today’s digital world, where email communication is vital for businesses, making sure that emails are delivered reliably is of key importance. However, the constant problem of spam, malicious activities, and compromised systems can disrupt this crucial aspect of modern communication.
This is where Real-time Blackhole Lists (RBLs) come into play, along with the innovative RBL monitoring feature in 360 Monitoring. Let’s explore what this means and how it benefits different types of users.
What is Blocklist Monitoring?
Real-time Blackhole Lists (RBLs) are carefully curated lists of IP addresses that have a bad reputation for sending spam, being involved in malicious activities, or having compromised security. They act as guides for email servers to decide whether to accept, reject, or label incoming emails as spam. If an IP address is on an RBL, it’s a warning sign that there might be problems with email delivery.
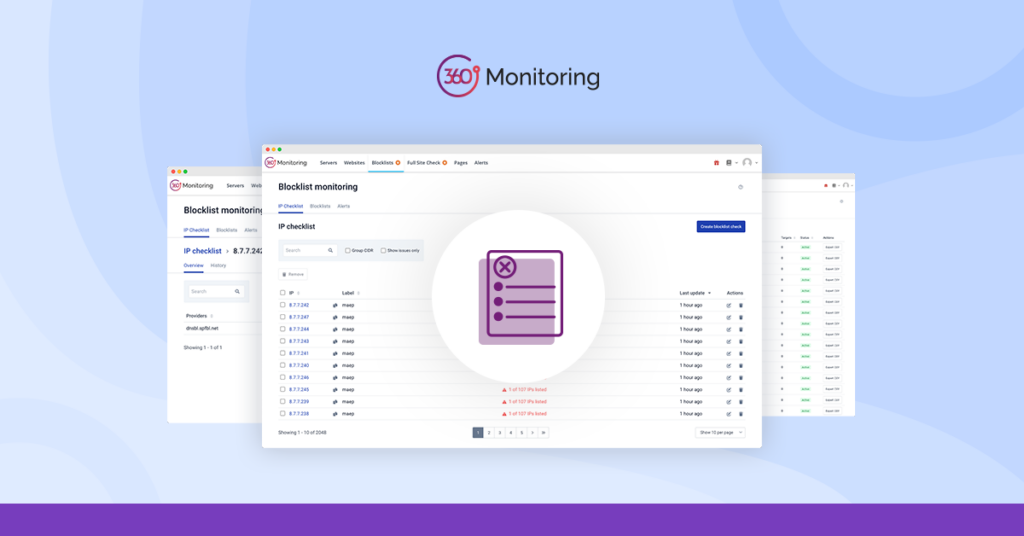
Blocklist Monitoring in 360 Monitoring
The recently introduced Blocklist Monitoring feature in 360 Monitoring represents a significant advancement in how we manage email deliverability. It automates the process of monitoring and updating these lists, ensuring that email communication flows smoothly. Ensuring that emails consistently reach their intended recipients is paramount for businesses of all sizes.
Whether you are a small and medium-sized enterprise (SME) or a freelance professional offering online services, Blocklist Monitoring tirelessly works behind the scenes to keep your emails from being diverted into spam folders or, worse, rejected entirely.
For SMEs, this translates into uninterrupted communication with clients, while freelancers can breathe easy knowing their messages reliably reach their clients’ inboxes. Let’s dive into why Blocklist Monitoring is essential and how it helps different types of users.
Who can benefit from Blocklist Monitoring feature?
1. Everyday Businesses | Small and Medium-sized Companies
Key Benefit: Cost-effective security monitoring, simplified detection of threats, and protection against common cyber dangers.
Ensuring that emails consistently reach their intended recipients is paramount for businesses of all sizes. For small and medium-sized companies, time is precious. The Blocklist Monitoring feature in 360 Monitoring saves them valuable time by automatically checking and updating these lists.
By monitoring RBLs, these businesses can quickly identify and solve email delivery issues, ensuring important messages reach their intended recipients. This simplified threat detection lets them focus on their core business without compromising security.
2. IT Administrators (Managing Infrastructure)
Key Benefit: Better detection of threats, real-time monitoring, and proactive security measures.
IT administrators play a crucial role in keeping digital systems safe and stable. Blocklist Monitoring boosts their ability to detect threats by providing real-time monitoring of IP blocklist listings. This helps them identify potential reputation issues and take action to prevent problems. With Blocklist Monitoring, IT administrators can improve their ability to respond to incidents and ensure email communication runs smoothly.
3. IT Managers (Overseeing Operations and Security)
Key Benefit: Improved understanding of security, better incident response.
Blocklist Monitoring saves IT managers time by automating the process of checking these lists. This proactive approach helps prevent email delivery issues and ensures a strong response when incidents occur. IT managers can assess the reputation of their IP addresses and take steps to maintain a good reputation.
4. Web and Marketing Agencies
Key Benefit: Better email delivery, protection of client reputation, and increased professionalism.
Web and marketing agencies can now avoid the manual work of checking these lists, thanks to Blocklist Monitoring. It provides real-time updates and immediate alerts, saving them time and effort. Maintaining a good email reputation is crucial for their clients, and Blocklist Monitoring helps them quickly identify any IP blocklist listings connected to their clients’ email systems. Resolving these issues promptly protects their clients’ reputation and demonstrates professionalism.
5. Freelancers
Key Benefit: Reliable email delivery, satisfied clients, and fewer support tickets related to email problems.
Freelancers can now be confident that their emails will be delivered reliably, thanks to automated continuous monitoring. They no longer need to worry about their emails being blocked just after they’ve checked for issues.
6. Hosting Providers and VPS Hosts
Key Benefit: Enhanced security offerings, improved hosting security, and increased trust from customers.
For hosting providers, Blocklist Monitoring in 360 Monitoring becomes a valuable additional service. It saves time by automating the monitoring and updating of these lists. By actively monitoring RBLs, hosting providers can ensure that their IP addresses and infrastructure stay off blocklists, reducing the risk of email delivery issues for their clients. This improves overall hosting security and gives customers confidence that their emails will arrive safely.
7. VPS Hosts
Key Benefit: Improved security measures, protection of customer data, and stronger hosting infrastructure.
VPS hosts can save time and effort by relying on automated notifications of potential issues with their server’s reputation. Blocklist Monitoring helps them identify IP blocklist listings associated with their servers, allowing them to take quick action to mitigate risks. This ensures customer data is protected, and hosting infrastructure remains secure.
Quick Summary
In conclusion, Blocklist Monitoring feature in 360 Monitoring benefits online businesses and hosting providers. Businesses can secure email delivery, proactive threat detection, and improved incident response.
Hosting providers and VPS hosts gain enhanced security offerings, improved hosting security, and increased customer trust. Blocklist Monitoring acts as a guardian, ensuring uninterrupted email communication and upholding a secure and trustworthy online presence.